Python Openssl Generate Rsa Key Pair
- May 29, 2016 The most effective and fastest way is to use command line tools: codeopenssl genrsa -out mykey.pem 4096 openssl rsa -in mykey.pem -pubout mykey.pub /codeIt’ll generate RSA key pair in code mykey.pem/code and code mykey.pub/code.
- This JCE provider 'FakeSigningProvider' enables you to create your own RSA key pair and X.509 code signing certificate. The provider replaces one of the JVM built-in certificates by the custom one. Developers can perform JCE code signing of their own JCE providers using their custom RSA key pair.
Several tools exist to generate SSH public/private key pairs. The following sections show how to generate an SSH key pair on UNIX, UNIX-like and Windows platforms.
Generating an SSH Key Pair on UNIX and UNIX-Like Platforms Using the ssh-keygen Utility
Use Openssl To Generate Key Pair
I want to generate an RSA public public key file using openssl (or other tools) having public modulus and exponent, so i can use it later to encrypt files i have this: the modulus: '. OpenSSL Outlook PEM PFX/P12 POP3 PRNG. CkPython example code showing how to generate an RSA public/private key pair and export to PEM files. Chilkat Python Downloads. Since OpenSSL is a collection of modules we specify genpkey to generate a private key. The -algorithm option specifies which algorithm we want to use to generate the key (RSA in this case), -out specifies the name of the output file, and -pkeyopt allows us to set the value for specific key options. In this case the length of the RSA key in bits. Sep 25, 2019 Hi @IOTrav The sample application shows an example how to generate a key pair into a context ( rsa or ecp ). Once you have the relevant context, you can use this context to write both the public key and the private key in PEM format, using mbedtlspkwritepubkeypem and mbedtlspkwritekeypem.
UNIX and UNIX-like platforms (including Solaris and Linux) include the ssh-keygen utility to generate SSH key pairs.
- Navigate to your home directory:
- Run the ssh-keygen utility, providing as
filenameyour choice of file name for the private key:The ssh-keygen utility prompts you for a passphrase for the private key.
- Enter a passphrase for the private key, or press Enter to create a private key without a passphrase:
Note:
While a passphrase is not required, you should specify one as a security measure to protect the private key from unauthorized use. When you specify a passphrase, a user must enter the passphrase every time the private key is used.
The ssh-keygen utility prompts you to enter the passphrase again.
- Enter the passphrase again, or press Enter again to continue creating a private key without a passphrase:
- The ssh-keygen utility displays a message indicating that the private key has been saved as
filenameand the public key has been saved asfilename.pub. It also displays information about the key fingerprint and randomart image.
Generating an SSH Key Pair on Windows Using the PuTTYgen Program
The PuTTYgen program is part of PuTTY, an open source networking client for the Windows platform.
- Download and install PuTTY or PuTTYgen.
To download PuTTY or PuTTYgen, go to http://www.putty.org/ and click the You can download PuTTY here link.
- Run the PuTTYgen program.
- Set the Type of key to generate option to SSH-2 RSA.
- In the Number of bits in a generated key box, enter 2048.
- Click Generate to generate a public/private key pair.
Prtg 18 license key generator. As the key is being generated, move the mouse around the blank area as directed.
- (Optional) Enter a passphrase for the private key in the Key passphrase box and reenter it in the Confirm passphrase box.
Note:
While a passphrase is not required, you should specify one as a security measure to protect the private key from unauthorized use. When you specify a passphrase, a user must enter the passphrase every time the private key is used.
- Click Save private key to save the private key to a file. To adhere to file-naming conventions, you should give the private key file an extension of
.ppk(PuTTY private key).Note:
The.ppkfile extension indicates that the private key is in PuTTY's proprietary format. You must use a key of this format when using PuTTY as your SSH client. It cannot be used with other SSH client tools. Refer to the PuTTY documentation to convert a private key in this format to a different format. - Select all of the characters in the Public key for pasting into OpenSSH authorized_keys file box.
Make sure you select all the characters, not just the ones you can see in the narrow window. If a scroll bar is next to the characters, you aren't seeing all the characters.
- Right-click somewhere in the selected text and select Copy from the menu.
- Open a text editor and paste the characters, just as you copied them. Start at the first character in the text editor, and do not insert any line breaks.
- Save the text file in the same folder where you saved the private key, using the
.pubextension to indicate that the file contains a public key. - If you or others are going to use an SSH client that requires the OpenSSH format for private keys (such as the
sshutility on Linux), export the private key:- On the Conversions menu, choose Export OpenSSH key.
- Save the private key in OpenSSH format in the same folder where you saved the private key in
.ppkformat, using an extension such as.opensshto indicate the file's content.
While Encrypting a File with a Password from the Command Line using OpenSSLis very useful in its own right, the real power of the OpenSSL library is itsability to support the use of public key cryptograph for encrypting orvalidating data in an unattended manner (where the password is not required toencrypt) is done with public keys.
So I’m going to share what I found and how it can be implemented. Generate aes key from password c key. However, I didn’t find very many write-ups on how to do the same thing using AES encryption.
The Commands to Run
Generate a 2048 bit RSA Key
You can generate a public and private RSA key pair like this:
openssl genrsa -des3 -out private.pem 2048
That generates a 2048-bit RSA key pair, encrypts them with a password you provideand writes them to a file. You need to next extract the public key file. You willuse this, for instance, on your web server to encrypt content so that it canonly be read with the private key.
Export the RSA Public Key to a File
Openssl Generate Keypair
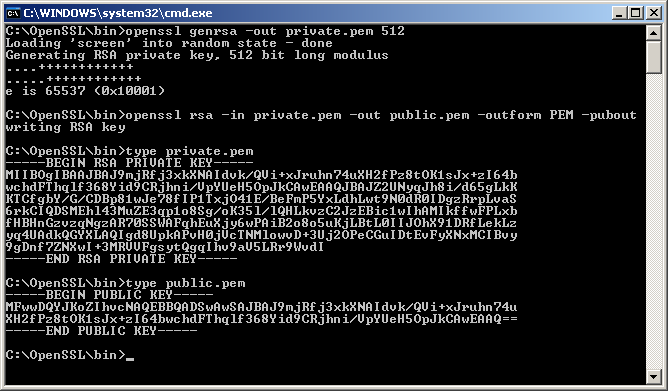
This is a command that is
openssl rsa -in private.pem -outform PEM -pubout -out public.pem
The -pubout flag is really important. Be sure to include it.
Next open the public.pem and ensure that it starts with-----BEGIN PUBLIC KEY-----. This is how you know that this file is thepublic key of the pair and not a private key.
To check the file from the command line you can use the less command, like this:
less public.pem
Do Not Run This, it Exports the Private Key
A previous version of the post gave this example in error.
openssl rsa -in private.pem -out private_unencrypted.pem -outform PEM
The error is that the -pubout was dropped from the end of the command.That changes the meaning of the command from that of exporting the public keyto exporting the private key outside of its encrypted wrapper. Inspecting theoutput file, in this case private_unencrypted.pem clearly shows that the keyis a RSA private key as it starts with -----BEGIN RSA PRIVATE KEY-----.
Visually Inspect Your Key Files
It is important to visually inspect you private and public key files to makesure that they are what you expect. OpenSSL will clearly explain the nature ofthe key block with a -----BEGIN RSA PRIVATE KEY----- or -----BEGIN PUBLIC KEY-----.
You can use less to inspect each of your two files in turn:
less private.pemto verify that it starts with a-----BEGIN RSA PRIVATE KEY-----less public.pemto verify that it starts with a-----BEGIN PUBLIC KEY-----
The next section shows a full example of what each key file should look like.
The Generated Key Files
The generated files are base64-encoded encryption keys in plain text format.If you select a password for your private key, its file will be encrypted withyour password. Be sure to remember this password or the key pair becomes useless.
The private.pem file looks something like this:
The public key, public.pem, file looks like:
Protecting Your Keys
Depending on the nature of the information you will protect, it’s important tokeep the private key backed up and secret. The public key can be distributedanywhere or embedded in your web application scripts, such as in your PHP,Ruby, or other scripts. Again, backup your keys!
Remember, if the key goes away the data encrypted to it is gone. Keeping aprinted copy of the key material in a sealed envelope in a bank safety depositbox is a good way to protect important keys against loss due to fire or harddrive failure.
Oh, and one last thing.
If you, dear reader, were planning any funny business with the private key that I have just published here. Know that they were made especially for this series of blog posts. I do not use them for anything else.
Found an issue?
Rietta plans, develops, and maintains applications.
Learn more about our services or drop us your email and we'll e-mail you back.