Gpg Generate Key In Batch Mode
Encryption/decryption commands
Jun 28, 2019 gpg -full-generate-key. Running the above command will take you through several questions. Two of them will involve choosing userid and passphrase. Keep them safe. Export Public Key. Gpg -export -a userid public.key. Export Private Key. Gpg -pinentry-mode=loopback -batch -passphrase secret-export-secret-keys userid private.key. GnuPG uses a somewhat more sophisticated scheme in which a user has a primary keypair and then zero or more additional subordinate keypairs. The primary and subordinate keypairs are bundled to facilitate key management and the bundle can often be considered simply as one keypair.
Gpg Generate Key In Batch Mode Software
- To encrypt a plaintext file with the recipient's public key:
- To sign a plaintext file with your secret key:
- To sign a plaintext file with your secret key and have the outputreadable to people without running GPG first:
- To sign a plaintext file with your secret key, and then encrypt itwith the recipient's public key:
- To decrypt an encrypted file, or to check the signature integrityof a signed file:
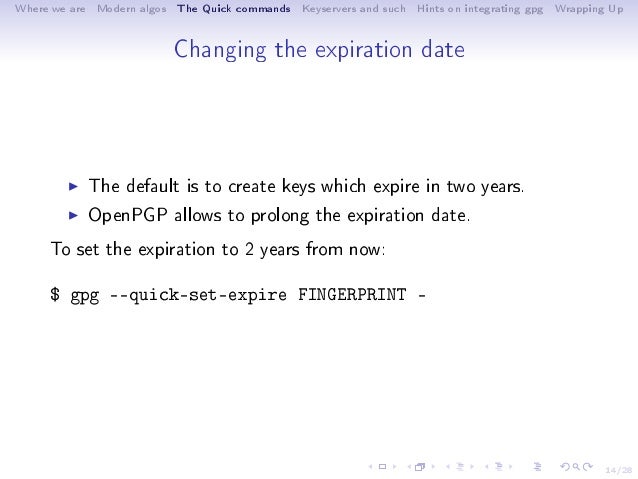
- Generate a new key pair. This command is normally only used interactive. There is an experimental feature which allows to create keys in batch mode. See the file doc/DETAILS in the source distribution on how to use this.-edit-key name. Present a menu which enables you to do all key.
- The Red Hat Customer Portal delivers the knowledge, expertise, and guidance available through your Red Hat subscription. Creating GPG Keys Using the Command Line Red.
Key management commands
- To generate your own unique public/secret key pair:
- To add a public or secret key file's contents to your public orsecret key ring:
- To extract (copy) a key from your public or secret key ring:
or
- To view the contents of your public key ring:
- To view the 'fingerprint' of a public key, to help verify it overthe telephone with its owner:
- To view the contents and check the certifying signatures of yourpublic key ring:
- To edit a key:
- To remove a key or just a userid from your public key ring:
- To permanently revoke your own key, issuing a key compromise certificate:
- To disable or re-enable a public key on your own public key ring:
or Sftp generate public key windows 7.
Esoteric commands
- To create a signature certificate that is detached from the document:
- To detach a signature certificate from a signed message
Command options that can be used in combination with other command options
- To produce a ciphertext file in ASCII format, just add the -aoption when encrypting or signing a message or extracting a key:
- To specify a recipient, add the -r option followed by a user id:
- To specify an output file, add the -o option followed by a filename:
| Key-Type: 1 |
| Key-Length: 2048 |
| Subkey-Type: 1 |
| Subkey-Length: 2048 |
| Name-Real: Root Superuser |
| Name-Email: root@handbook.westarete.com |
| Expire-Date: 0 |
| # Generate the key |
| gpg --batch --gen-key gen-key-script |
commented Feb 13, 2014
Here's a page that describes the options for the gen-key script: http://www.gnupg.org/documentation/manuals/gnupg-devel/Unattended-GPG-key-generation.html |
commented Feb 13, 2014
Originally I had a couple extra steps to use rng-tools to seed entropy from /dev/urandom. Apparently this is a bad idea because it will just feed bytes regardless of whether there's enough entropy. Here's where I got the original idea, and the subsequent discussion of why it's bad. For new machines, we should generate the keys on our laptops where there's much more entropy to draw from, and then transfer them to the new server, just like we're currently doing with the encrypted data bag secret. |
commented Feb 19, 2018

This is awesome, thank you. |
Gpg Generate Key In Batch Mode 2017
commented Jan 23, 2019
I configured libvirt tu use /dev/urandom of the host: https://libvirt.org/formatdomain.html#elementsRng |
commented Apr 9, 2019 • edited
edited
Thanks that was really helpful |
